
Blog
Privacy Codes Explained: Securing Your Radio Conversations

In an age where dialogue is both instantaneous and ubiquitous, the importance of safeguarding our conversations has never been more pronounced. Imagine transmitting critical information over the airwaves, only to find it intercepted by an uninvited listener.This scenario highlights the vital need for privacy in radio communications, a realm where clarity and security must coexist. Enter privacy codes—designed to enhance the confidentiality of your discussions by adding an extra layer of protection against eavesdropping. In this article, we will delve into the intricacies of privacy codes, exploring how they function, their variations across different radio platforms, and best practices for effective implementation. Whether you’re chatting with your team on the job site or sharing adventures over a walkie-talkie, understanding the utility of these codes can transform your radio experience from one of vulnerability to one of fortified connection. Join us as we unravel the details behind securing your radio conversations in a world where every word counts.
Table of Contents
- Understanding Privacy Codes and Their Importance in Radio Communication
- Decoding the Types of Privacy Codes and Their Functions
- Best Practices for Implementing Privacy codes in Your Radio Use
- Navigating Legalities and Ethical Considerations in Secure Communications
- Q&A
- Closing Remarks
Understanding Privacy Codes and Their Importance in radio Communication
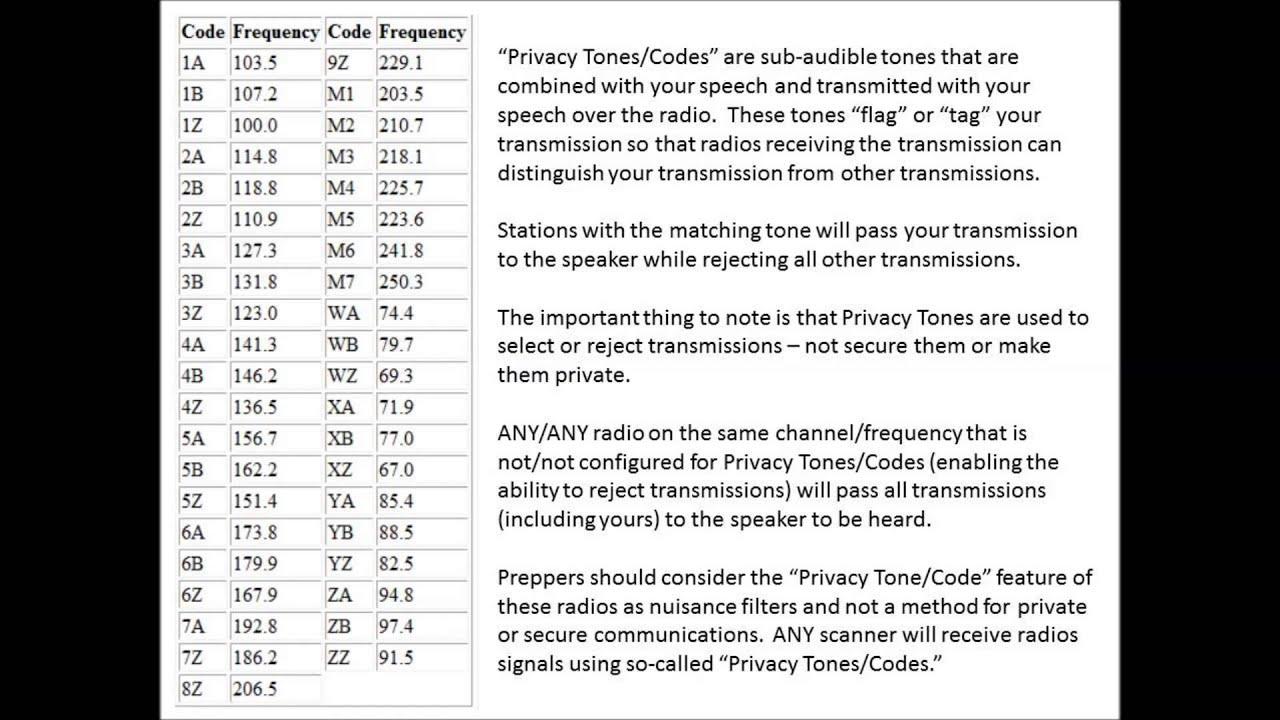
In the world of radio communication, privacy codes serve as essential tools for enhancing the security and confidentiality of conversations. These codes, often referred to as CTCSS (Continuous Tone-Coded squelch System) or DCS (Digital Coded squelch), function by adding a layer of encryption to standard radio signals. This means that even if someone is tuned into the same channel, they won’t be able to here your transmission unless their device is set to the same privacy code. By utilizing these codes, users can substantially reduce eavesdropping, ensuring that sensitive discussions remain private and secure. In high-stakes environments such as law enforcement, medical emergencies, or private events, these codes act as a safeguard against potential threats or leaks of sensitive information.
Understanding the mechanics behind privacy codes reveals their broader implications in maintaining efficient communication. Implementing these codes can lead to a range of benefits, including:
- Reduction of interference: By filtering out unwanted noise from other users on the channel.
- Enhanced confidentiality: Protecting sensitive discussions from prying ears.
- Streamlined communication: Allowing groups to converse without overlap or interruptions from other users.
Along with these advantages, privacy codes can be matched and customized according to group needs. The following table illustrates common privacy codes along with their respective meanings:
| Code | Description |
|---|---|
| 67.0 Hz | Standard Privacy Code |
| 82.5 Hz | Commonly Used in Business |
| 136.5 Hz | Privacy for Emergency Services |

Decoding the Types of Privacy Codes and Their Functions
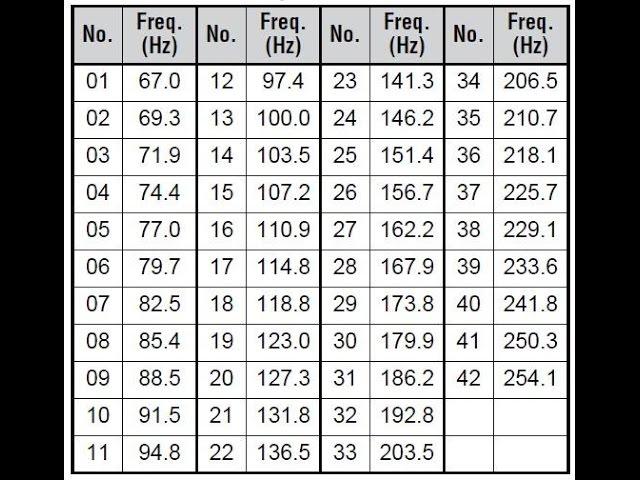
When it comes to the engaging realm of radio communications, privacy codes serve as indispensable tools for enhancing security and ensuring confidentiality. These codes function as additional layers of protection, allowing radio users to communicate without the risk of eavesdropping. The primary types of privacy codes include CTCSS (Continuous tone-Coded Squelch System) and DCS (Digital-Coded Squelch). Each of these codes operates by sending a specific tone along with the radio signal, which enables receivers to filter out unwanted transmissions, effectively creating a private channel for legitimate communications.
CTCSS works by transmitting a sub-audible tone, ensuring that only radios programmed to recognize that tone will activate the audio output. On the other hand,DCS sends a unique digital code,which provides a higher level of {content security}. Below is a brief table showcasing the key differences between CTCSS and DCS:
| Feature | CTCSS | DCS |
|---|---|---|
| Type of Coding | Analog | Digital |
| Tone Frequency | Low-frequency sub-audible tone | Digital coded signal |
| Privacy Level | Moderate | Higher |
Understanding these privacy codes is essential for anyone looking to keep their radio conversations private and secure. Beyond mere communication, these tools empower users to control the flow of information in a way that’s both effective and discreet. Whether you are coordinating a local event or conducting sensitive business discussions, leveraging the right privacy code can greatly enhance your communication strategy.
Best Practices for Implementing Privacy Codes in Your Radio Use
Implementing privacy codes effectively requires careful planning and execution. Start by assessing your communication environment, taking into consideration the nature of the conversations, the potential vulnerabilities, and the specific privacy needs of your team. It’s critical to involve all relevant stakeholders in this process, as their insights will shape the most effective code for your operations. Provide comprehensive training sessions for all users, ensuring that they understand the purpose of the codes, how to implement them, and the importance of adhering to them consistently. Make this training engaging through interactive elements, such as role-playing scenarios that simulate real-world applications of privacy codes.
Moreover, keep in mind the necessity of regularly reviewing and updating your privacy codes as your operational needs evolve. Establish a clear schedule for revisits and assessments, and create a feedback loop that allows team members to report any issues or suggest improvements based on their experiences. Ensure that the codes are not just bureaucratic hurdles but are integrated into daily radio habits. To facilitate this, consider developing a reference chart that summarizes the key privacy protocols for speedy access. This chart can serve as a handy tool to reinforce the habit of using codes and understanding their significance in maintaining secure communications.
| Privacy Code | Application | Frequency of Use |
|---|---|---|
| Code 1 | Emergency Communication | Always |
| Code 2 | Routine Updates | Daily |
| Code 3 | Confidential Messages | As Needed |

navigating Legalities and Ethical Considerations in Secure Communications
When engaging in secure radio communications, it is crucial to understand the legal frameworks that govern privacy and data protection. Different jurisdictions have varying regulations regarding the transmission and storage of communication data, making it vital to ensure compliance. Key legal considerations include:
- Data Protection Laws – Regulations such as GDPR in Europe impose strict controls on personal data.
- federal Communications Commission (FCC) – In the U.S., compliance with FCC regulations on radio communications is essential.
- Eavesdropping and Interception Laws – Many regions have laws prohibiting unauthorized access to communications.
Beyond legal considerations, ethical dimensions also play a significant role in the implementation of secure communications.Organizations must foster a culture of respect for personal privacy and integrity while using radio technologies. This involves:
- Transparency – Clearly communicate how communication data will be used and safeguarded.
- Informed Consent – Ensure that all parties involved are aware of and agree to any monitoring measures.
- Data Minimization – Collect only the information that is necessary for the specific purpose of communication.
| Legal Aspect | Ethical Consideration |
|---|---|
| Compliance with Local Laws | Prioritize user privacy |
| Data Retention policies | Ensure responsible data usage |
| Unauthorized Access Prevention | Maintain transparency with users |
Q&A
Q&A: Privacy Codes Explained – Securing Your Radio Conversations
Q1: What are privacy codes, and why are they crucial for radio communications?
A1: Privacy codes, frequently enough referred to as subcodes or CTCSS (Continuous Tone-Coded Squelch System), are essentially audio tones that allow radio users to filter out unwanted conversations. When used, these codes ensure that only those on the same frequency and possessing the correct tone can hear each other’s conversations. This adds an essential layer of privacy and security to radio communications, making it especially critically important for businesses, emergency services, or anyone seeking to maintain confidentiality in their discussions.
Q2: How do privacy codes work in practice?
A2: Privacy codes work by sending a specific subaudible tone along with the radio transmission. when a radio receiver is set to a certain privacy code, it will only unmute the audio when it detects the corresponding tone. If another transmission occurs on the same frequency without the tone, the receiver remains silent. This system effectively filters out irrelevant chatter from other users on the same channel, which is crucial in crowded communication environments.
Q3: Are privacy codes foolproof?
A3: While privacy codes significantly enhance the security of radio communications, they are not entirely foolproof. Savvy listeners equipped with the right equipment can potentially detect the frequencies and tones being used. Thus, privacy codes should be viewed as a practical measure rather than an absolute safeguard. For truly sensitive conversations, additional measures, like encrypted communications, are advisable.
Q4: How do I choose the right privacy code for my communications?
A4: Choosing the right privacy code involves considering the needs of your group. Most radios come with a list of standard privacy codes. To ensure effective communication, select a code that is less likely to be used by others in your vicinity. A little experimentation might be necessary to find a code that minimizes interference while still allowing your group to communicate effectively.
Q5: What are common misconceptions about using privacy codes?
A5: One common misconception is that privacy codes provide total anonymity. While they can help reduce unwanted eavesdropping,all radio communications can potentially be intercepted. Another myth is that privacy codes are only for professional or emergency radios—they can actually be beneficial for anyone using radios, from outdoor enthusiasts to event organizers, looking to keep their conversations discreet.
Q6: Can privacy codes be used for all types of radios?
A6: Privacy codes are compatible with most modern two-way radios, including FRS (Family Radio Service) and GMRS (General Mobile Radio Service) devices.However, not all radios are equipped with privacy code features, so it’s essential to check the specifications before buying or using a device for this purpose.
Q7: What’s the future of privacy codes in radio communication?
A7: The future of privacy codes is likely to evolve alongside technological advancements in communication. With the rise of digital radios,we may see enhanced encryption methods and more sophisticated privacy features that go beyond conventional tones. As user demand for privacy grows, the expected growth of more robust solutions will pave the way for greater security in radio communications.
Q8: Where can I learn more about implementing privacy codes?
A8: To learn more about implementing privacy codes, consider consulting the user manual of your specific radio model, joining online forums dedicated to radio communications, or attending workshops or training sessions on effective radio use. Many manufacturers also offer educational resources and support to help users understand and utilize privacy codes to their fullest potential.
Closing Remarks
As we navigate the intricate landscape of communication technology, the importance of safeguarding our exchanges becomes ever more paramount. privacy codes serve as a vital tool in this endeavor, offering an essential layer of security that allows us to converse freely without the fear of eavesdropping. As we’ve explored in this article, the implementation of these codes not only protects sensitive information but also reinforces our collective commitment to privacy in a world that often blurs the lines of confidentiality.
Whether you are a casual user or a seasoned professional, understanding privacy codes empowers you to take control of your communications, ensuring that each conversation remains a sanctuary of trust and discretion. As you venture forward in your radio communications, remember that knowledge is your first line of defense. The next time you engage in a dialogue, let the art of encryption guide you, and rest assured knowing that your messages are cloaked in the security of privacy codes. in an era where information is both invaluable and vulnerable, let us choose to protect it with intention and awareness.












